Remove TeslaCrypt 3.0 ransomare and decrypt .ttt, .xxx, .micro files
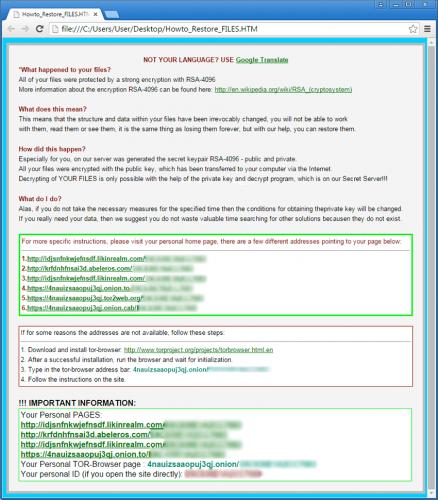 The rogue malware campaign affiliated with TeslaCrypt ransomware has gotten fine-tuned recently. With the new 3.0 version of the virus coming to the fore, security experts and common users should be aware of the changes made to its structure. These include the modified key exchange algorithm and the updated list of file extensions accompanying the infection. In particular, the locked files are now appended with the following extensions: .ttt, .xxx, or .micro. As earlier, the infection brings up a ransom notification in a file named Howto_Restore_FILES.HTM (.BMP / .TXT) that says “All of your files were protected by a strong encryption with RSA-4096”. The victim is told to click one of the Tor gateway links, which are unique to the specific occurrence, and pay a ransom of about 500 USD to launch data decryption procedure. In other words, the redemption routine involves an anonymous decryption site that stores the respective private key. Full story: http://nabzsoftware.com/types-of-threats/teslacrypt-3-0
The rogue malware campaign affiliated with TeslaCrypt ransomware has gotten fine-tuned recently. With the new 3.0 version of the virus coming to the fore, security experts and common users should be aware of the changes made to its structure. These include the modified key exchange algorithm and the updated list of file extensions accompanying the infection. In particular, the locked files are now appended with the following extensions: .ttt, .xxx, or .micro. As earlier, the infection brings up a ransom notification in a file named Howto_Restore_FILES.HTM (.BMP / .TXT) that says “All of your files were protected by a strong encryption with RSA-4096”. The victim is told to click one of the Tor gateway links, which are unique to the specific occurrence, and pay a ransom of about 500 USD to launch data decryption procedure. In other words, the redemption routine involves an anonymous decryption site that stores the respective private key. Full story: http://nabzsoftware.com/types-of-threats/teslacrypt-3-0
Advertise on APSense
This advertising space is available.
Post Your Ad Here
Post Your Ad Here
Comments