Insecure Storage of Sensitive Information
Description of the problem: Insecure Storage
Most web
applications have a need to store sensitive information, either in a database
or on a file system somewhere. The information might be passwords, credit card
numbers, account records, or proprietary information. Frequently, encryption
techniques are used to protect this sensitive information. While encryption has
become relatively easy to implement and use, developers still frequently make
mistakes while integrating it into a web application. Developers may
overestimate the protection gained by using encryption and not be as careful in
securing other aspects of the site. A few areas where mistakes are commonly
made include:
- Failure
to encrypt critical data
- Insecure
storage of keys, certificates, and passwords
- Improper
storage of secrets in memory
- Poor
sources of randomness
- Poor
choice of algorithm
- Attempting
to invent a new encryption algorithm
- Failure
to include support for encryption key changes and other required
maintenance procedures
The impact
of these weaknesses can be devastating to the security of a website. Encryption
is generally used to protect a site's most sensitive assets, which may be
totally compromised by a weakness.
Read about other security problems on Web Development: Security Misconfiguration
We have used JSP, Tomcat and MySQL to demonstrate the
insecure direct object reference where user is able to get the access of
information without having an authentication.
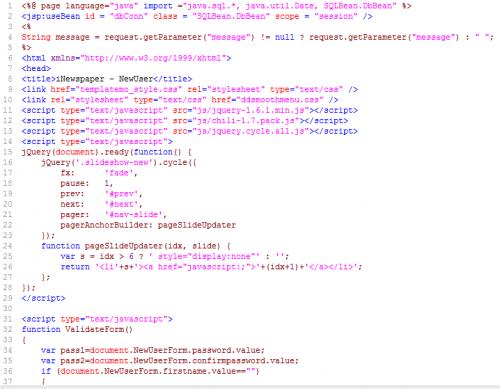
Let’s consider the create user example of any web application which posts data from create user page to intermediate processing jsp page which processes this data to the database. Below is code screen shot for createuser.jsp.
After providing the required information to create user, this page is sending information to another processing page in JSP which will eventually create the user in database. Below is the code screen shot for the same.
Evaluation of the result
In the above
database screen shot it is clearly visible that passwords are being stored in
database as plain text and any one who has access of database, can retrieve
this information. This information can be misused. If attacker gets this information, he can
easily navigate the system and make any kind of modification in the available
information.
Insecure Storage defend
mechanism
The easiest
way to protect information from direct access, either use a encruption
mechanism to store confidential data or use a one-way function, such as SHA-1,
to hash the passwords.
If
cryptography must be used, choose a library that has been exposed to public
scrutiny and make sure that there are no open vulnerabilities.
Encapsulate the cryptographic functions that are used and review the code carefully. Be sure that secrets, such as keys, certificates, and passwords, are stored securely. To make it difficult for an attacker, the master secret should be split into at least two locations and assembled at runtime.
Post Your Ad Here
Comments