5 Popular Security Tricks That Budding IOS Developers Must Learn
Apps these days store tons of user data. As the cliché goes, if what you are consuming is free, then you are the product. Customer data has been a focal point of discussion for years. From analytical companies to ad services, everyone wants to have a good look at the behavioral patterns of their target customers for them to penetrate better.
Right from domain passwords to one time passwords, health tracking to confidential emails, different apps on our phones store different kinds of data. The exchange of data is vulnerable to various kinds of threats. Apple is very much popular for providing a robust and stubborn infrastructure that goes through their own checklist before getting any sort of data exchange approval. Even then your data is not 100% secure.
Different Types of Possible Data Threats to Your IOS
Attackers are innovating and almost catching up the developers. There will never be a promised pattern of attacks but there are categorically four different vulnerable channels that can attract the theft.
Threat from hardware: There are more than one ways to interact with your IOS devices. Voice, text and camera lenses are a notable few of them. Attackers can attempt to take over your lenses, store your voice input or decrypt the messages. Allowing permissions to all hardware to dubious apps can cause this.
Threat from network: Spam phone calls or unsafe wifi networks can result in attackers getting access to your precious data. Although this might need massive unconscious assistance from your end, network related threats are still a very common occurrence.
Threat from web: Web browsing is still a popular practice and the enhanced web application experience aids to it. Browsers are pretty much a favorite hangout place for hackers and you may store unnecessary fishing data in your device without knowing.
Threat from apps: Apps these days want total control over your phones and ask for all sorts of permission like location, voice, gallery, phone log etc. Allowing permissions to dubious apps can result in attacks from spyware of malware and you may expose your sensitive data to them.
Possible Techniques to Prevent or Fight Threats
Now that we know the possible ends from which you might face the attack, let us venture the possibilities to fight or prevent these attacks. There will never be anything like a 100% secure experience as the battle between hackers and developers always remains a heavy one. However, your IOS mobile app development company following the below mentioned practices and adapting to a few tweaks and tricks can ensure that the attackers are at least playing the game of catching up.
API Protection: Although every version since IOS 4.0 has in-built functions of encrypting the files in app directory, it is worth noting that this encryption is compatible with all database APIs like NSFileManager, CoreData, NSData & SQLite. The default setting encrypts all data until user authentication but this feature can be modified into 4 different levels notably with no protection at all, decryption with first authentication, decryption when the app opens the file for the first time and total encryption that ensures no data is accessible if the device is locked.
Another good practice to enhance API security is to use cryptographic exchanges to create unpredictable and inconsistent encryption that is hard to decrypt. Apple’s CryptoKit is a very useful developer option to do this task.
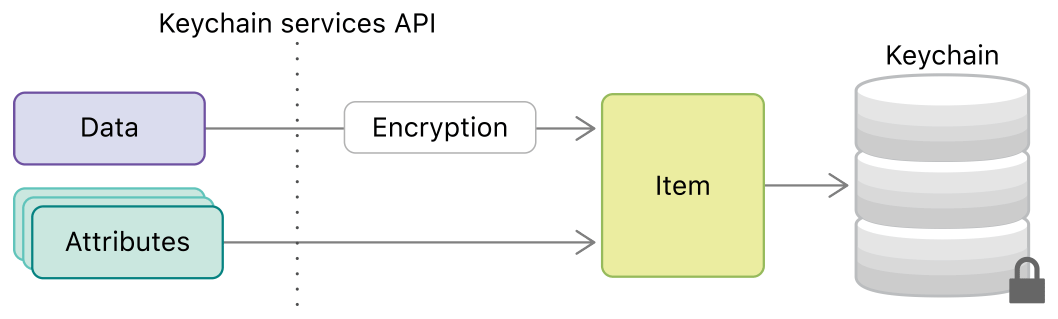
Keychain: The keychain technology works exactly like how the name suggests. It is a hardware driven storage place that comes along with keys that represent authentication. The keychain comes only with the key. Every app has its own space in the keychain where they can store small groups of data like passwords and verification certificates. Keychain allows you to not store individual encryption keys for different apps and you can trust the system to offer best security. The decryption of keychain can incorporate hardware security features like Face ID or biometric and the small section of storage can be both local as well as cloud.HTTPs: The most commonly used protocol between client & server - HTTP is not a safe protocol by its nature. The most common practice among attackers is to keep an eye on local sessions on your local network. IOS provides an additional layer called App Transport Security (ATS) that blocks any unsafe connection by using HTTPs and is validated and secured by TLS. In-app browsers are often at risk of attack and it is a recommended practice to use this configuration to avoid that.
Push Notifications: Push notifications are a great way to communicate for your app with its users. It is also a great way to notify the users with any new piece of information on your app. Apple has made it mandatory to use their APNs (Apple Push Notification Service) services if you wish to send push notifications from your app in the IOS. Furthermore, Apple also has a separate kit Push API of functions to perform the same via web browsers like Safari. These services essentially act as an encryption-decryption process that sends notifications on your screens without leaking your sensitive information to Apple’s servers.
End-to-end Encryption: The futuristic and perhaps the most honest method of deploying security measures is the end-to-end encryption. This is a generic technique that can be used for any functionality where you need to code and decode the information between client and server. The end-to-end technique does not use standard encryption methods and syntax like AES (Advanced Encryption Standard) or any other third party encryption standard groups. End-to-end encryption is achieved by using a cryptographic coding technique. The encryption is a code that cannot be repeated or copied and only the receiver gets the code to decrypt it. Once encrypted, the message cannot be decrypted anywhere else in the medium except for its destination. This is a more transparent technique that many instant messaging apps have incorporated. Any transfer of data between the user and the app server should be done using this method to avoid any third party intervention and any attempt of theft.
The Final Assessment
In this day and age of data ruling lifestyles, we must not let any attempt of spying or malpractices get the better of us. The resolution for this in IOS is a lengthy and culmination of multiple techniques but if used right, these combinations make your app a fortress. Data theft is a harsh reality of today’s world and it is safe to say that Apple provides the most sophisticated armor to battle that.


Comments (1)
Marketing Consultant...15
Business Growth Consultant
Dear APSense member, share a connection request with me.