North Korea’s Operating System Secretly Spies on You
We all know North Korea has one of the most oppressive
political systems in the world. Having a communist regime, the country and its
leaders are paranoid about pretty much everything. This article is solely
dedicated to their Red Star OS, an operating system developed for people living
in a government-controlled system.
Two German researchers, Florian Grunow and Niklaus Schiess, working
at the German IT security company ERNW GmbH, have been analyzing the code of
the Red Star OS version 3.0 since the past month. They presented the OS,
released online anonymously around a year ago, at the Chaos Communication
Congress in Hamburg, a meeting for security researchers and hackers. Their
findings are troubling, considering that the internet is designed for free
speech and expression.
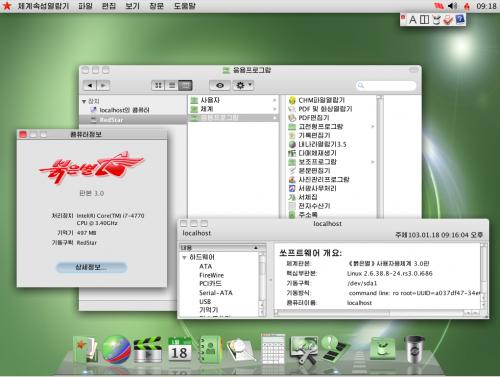
Based on the Linux distribution Fedora, the latest version
(3.0) was developed in 2013. As many probably know, Linux systems have the same
look and feel as that of Apple’s OS, not surprising considering that Kim Jong
Un, the leader of North Korea, has taken pictures with Macs just like his
Father.
There are many features present in the Red Star OS which are
similar to the Macintosh OS. It also includes a Korean word processor, a
calendar app, and one similar to Garageband for music.
In North Korea, a country where free internet is not
available, rich media like movies, music and written content is transferred
from person-to-person through USB drives and microSD cards. This makes it hard
to track the original uploader of the file. The Red Star OS tackles this issue
in an elusive manner. Hidden code in the OS watermarks each and every file and
identifies it with the user who first introduced that file into any Red Star
OS.
This implies that any file opened in the Red Star OS is
automatically associated with an identity. Thus, the government can track down
the user who has opened or created the file, along with the subsequent chain of
transfers, if any.
"It's definitely privacy invading, it's not transparent
to the user. It's done stealthily, and touches files you haven't even opened,"
Grunow said.
The OS also deletes undesired files without permission. Antivirus
software and firewalls protect the user from any attacks, foreign or domestic. Web
browsers are designed to access internal servers only. Encryption for the files
is purely custom-built. This might be due to the threat of any backdoors. Also,
if the system detects tampering with system files, the consequences might be
dire. The system shows an error and immediately reboots.
North Korea’s OS, in development since 2012, is not the only
‘foreign’ operating system developed by ‘secretive’ nations. Cuba, Russia and
China have made attempts at custom operating systems.
Post Your Ad Here
Comments