How to remove Alma Locker ransomware
Today we
will talk about the latest ransomware virus, called Alma Locker. This virus was
discovered a few days ago, and now we can say that it is one of the most
dangerous in recent months. Most ransomware, created in recent months have been
pretty poor quality, and breaking most of them took no more than a week. In
contrast, Alma Locker has no serious errors in its structure, and its
encryption is secure.
Alma Locker
was discovered by a researcher from Proofpoint, Darien Huss. Proofpoint said
that so far there is no free no way to decrypt the encrypted files, but work is
being done on it. Currently, the only safe way to restore files is the load of
backups. If you have not made a backup - your files are likely to be lost.
How Alma Locker penetrates the system and
encrypts the files
Alma Locker,
like other similar viruses is being distributed via e-mail. After infection,
the virus generates a random extension that will be added to the file names,
and computer ID, based on the serial number of the drive C and MAC address of
the first network interface. The virus can encrypt almost all the most popular
data extensions, this applies to audio and video files, text documents and
images. The program files remain safe. Alma Locker uses AES-128 encryption
algorithm, so if you are going to try to decrypt the files yourself - you will
fail.
When the
encryption process is finished, the virus displays a message to the user with
the requirements of redemption, referring to the payment to the TOR network
sites, and links to download the decryption software, after the payment of
ransom. Redemption amount is 1 Bitcoin, but fraudsters have established payment
term of 5 days. While it is not known what will happen at the end of this
period. It is likely that the amount of foreclosures will increase, or files
will be deleted (partially or completely).
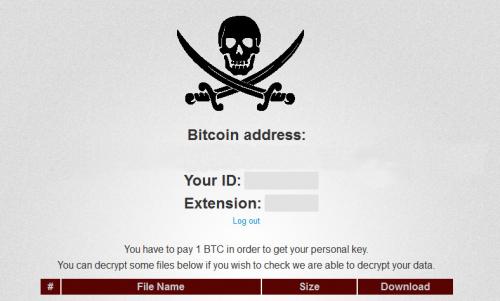
One of the
links in the message leads to the requirements of TOR on the site where your ID
is displayed, and the name of the extension that your files received. Also,
we'll see how many hours left before the completion of 5-day count. In the
design of the website the pirate flag "Jolly Roger" is used. Rather,
it is an allusion to the fact that, if user won’t pay the ransom, hackers will
make him to walk the plank, or he will be keelhauled and sent to feed the fish.
We hope that this is only a joke, and hackers won’t do such terrible things to
regular users.
Despite the
fact that Alma Locker is not an extraordinary virus, it is created with high
quality and, most likely, its hacking will take at least a few weeks. If you
are not going to pay hackers for data recovery, and want to protect other files
from encryption, you should remove the virus from your computer. The
step-by-step instructions to remove the virus, as well as options for file
recovery can be found in the extended article about how to remove Alma Locker
ransomware and restore the encrypted files.
Post Your Ad Here
Comments