2022 Update CompTIA Security+ SY0-601 Real Questions and Answers
The latest CompTIA Security+ SY0-601 Real Questions and Answers are new updated by PassQuestion team. Our SY0-601 Questions and Answers are designed to show you which approach is the best one for CompTIA Security+ exam preparation. Our SY0-601 Exam Dumps contain all of the real exam questions that may be found on the exam, allowing you to practice with them before the SY0-601 exam.These questions have been chosen based on the most likely as well as the greatest probability of appearing in the real SY0-601 exam. We're confident that our CompTIA Security+ SY0-601 Real Questions and Answers are the finest option for passing the exam with a high score.

CompTIA Security+ Certification
CompTIA Security+ is a global certification that validates the baseline skills necessary to perform core security functions and pursue an IT security career. Comp TIA Security+ is the first security certification IT professionals should earn. It establishes the core knowledge required of any cybersecurity role and provides a springboard to intermediate-level cybersecurity jobs. Security+ incorporates best practices in hands-on trouble-shooting to ensure security professionals have practical security problem-solving skills. Cybersecurity professionals with Security+ know how to address security incidents – not just identify them.
The CompTIA Security+ certification exam will verify the successful candidate has the knowledge and skills required to assess the security posture of an enterprise environment and recommend and implement appropriate security solutions; monitor and secure hybrid environments, including cloud, mobile, and IoT; operate with an awareness of applicable laws and policies, including principles of governance, risk, and compliance; identify, analyze, and respond to security events and incidents
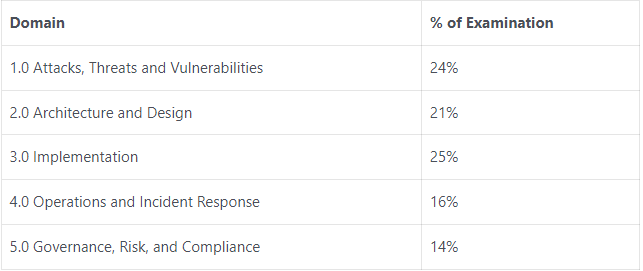
CompTIA Security+ SY0-601 Exam Objectives
The exam objectives are divided into the following domains, or general topic areas.
Check Online Update CompTIA Security+ SY0-601 Practice Exam Questions
Which of the following should a technician consider when selecting an encryption method for data that needs to remain confidential for a specific length of time?
A.The key length of the encryption algorithm
B.The encryption algorithm's longevity
C.A method of introducing entropy into key calculations
D.The computational overhead of calculating the encryption key
Answer : D
An organization recently discovered that a purchasing officer approved an invoice for an amount that was different than the original purchase order. After further investigation a security analyst determines that the digital signature for the fraudulent invoice is exactly the same as the digital signature for the correct invoice that had been approved Which of the following attacks MOST likely explains the behavior?
A.Birthday
B.Rainbow table
C.Impersonation
D.Whaling
Answer : D
A company is considering transitioning to the cloud. The company employs individuals from various locations around the world The company does not want to increase its on-premises infrastructure blueprint and only wants to pay for additional compute power required. Which of the following solutions would BEST meet the needs of the company?
A.Private cloud
B.Hybrid environment
C.Managed security service provider
D.Hot backup site
Answer : B
A SOC is currently being outsourced. Which of the following is being used?
A.Microservices
B.SaaS
C.MSSP
D.PaaS
Answer : C
A security analyst is investigating a phishing email that contains a malicious document directed to the company's Chief Executive Officer (CEO). Which of the following should the analyst perform to understand the threat and retrieve possible IoCs?
A.Run a vulnerability scan against the CEOs computer to find possible vulnerabilities
B.Install a sandbox to run the malicious payload in a safe environment
C.Perform a traceroute to identify the communication path
D.Use netstat to check whether communication has been made with a remote host
Answer : B
Which of the following BEST describes the method a security analyst would use to confirm a file that is downloaded from a trusted security website is not altered in transit or corrupted using a verified checksum?
A.Hashing
B.Salting
C.Integrity
D.Digital signature
Answer : C
Post Your Ad Here
Comments