Social Engineering Content
by Prashant Ojha Software TrainerSocial engineering is a method of misguiding users and
getting their personal information such as email id, contact number, sometimes
bank details and other personal details. It is directly related to phishing or
hacking. The purpose of using Social Engineering is to collect personal details
of users and use it for own benefits.
You can easily understand if someone has the access of user’s
sensitive information, what kind of misuse they can do.
However, it is social engineering content also used for
marketing purpose. For example, it might be used in marketing products and
political campaigns. With this method advertisers get to know about people’s
preferences and habits is gathered in advance. Then this information is used to
encourage people for buying stuff, opt in for subscriptions or to vote for a
particular person or political party.
Types of Social engineering content
As we know, social engineering is basically used to collect
data of users. So it could be only two types. One is to collect data and misuse
it and second one is to collect the data and use it for showing customized ads
by understanding user behaviour and habits. Social media ads preference works
on this algorithm. Whenever an advertiser creates an advertisement on social
platform, they customize advertisement audience and for that they could either
upload the existing data or choose between the provided options. Here people
use data collected by social engineering content techniques and customize their
audience.
However, social engineering content is generally known for fraud.
Types of social engineering attacks
Depending on the information, people who have the user data
could perform actions according to their choice. Let’s have a look on one
example below.
Example 1:

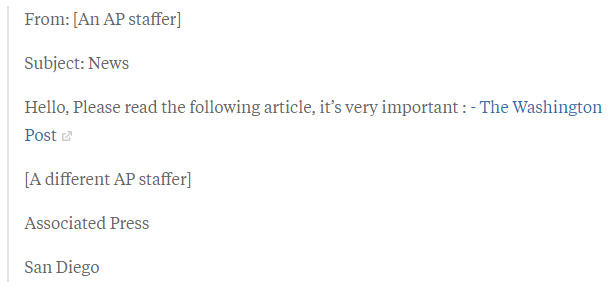
Back in 2013, the Associated Press Twitter account was taken
over by the Syrian Electronic Army (SEA), which posted the above tweet. Within
moments, the stock market dropped: the Dow Jones Industrial Average dropped 150
points as the tweet was re-tweeted, and the Standard & Poor’s 500 Index
fell about 1%, briefly losing USD$136 billion in value before quickly
rebounding.
They got the access of Associated Press Twitter account by a
phishing email.
Example 2:
RSA SecurID breach
Adobe Flash and vulnerabilities go hand in hand, which is
unfortunate for RSA’s SecurID. Back in 2011, RSA employees received two
phishing emails, which would ultimately lead to SecurID’s two-factor
authentication system being compromised – costing RSA $66 million.
RSA said in a blog post:

We can understand that social engineering content could create
different impact on user or companies according to people who collect data by
social engineering methods.
So far we have learned about types of social engineering,
how it works and its impact. Now let’s move on to the SEO aspects of social
engineering.
While using data collection forms on website or blogs
sometimes we encounter the problem of webmaster errors which says “Social
engineering Content Detected” on your website. It is not at all good for your website.

There are few steps which you need to follow in order to get
rid of this problem. Here is how to get rid of Social engineering detected problem.
Check webmasters for security issues.
Whenever we get a warning or information message from google
regarding social engineering content, we need to check the webmaster immediately
to understand the problem.
·
Go to : https://search.google.com/search-console/security-issues
·
Select the property from top left menu
·
Open the message
·
Find out the deceptive content and try to remove
it or make changes in it.
Next Step
Check for Third
Party Resources on your website
Ensure that any ads, images, or other embedded third-party
resources on your site's pages are not deceptive.
·
Note that ad networks may rotate the ads shown
on your site's pages. You therefore might need to refresh a page a few times
before you're able to see any social engineering ads appear.
·
Some ads may appear differently on mobile
devices and desktop computers. You can use the URL Inspection tool to view your
site in both mobile and desktop views.
·
Follow the third-party service guidelines
described below for any third-party services, such as payment services, that
you use in your site.
For more information on steps, follow the google guidelines
on Social
Engineering (Phishing and Deceptive Sites)
Sponsor Ads
Created on May 6th 2019 05:45. Viewed 415 times.




